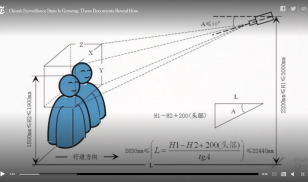
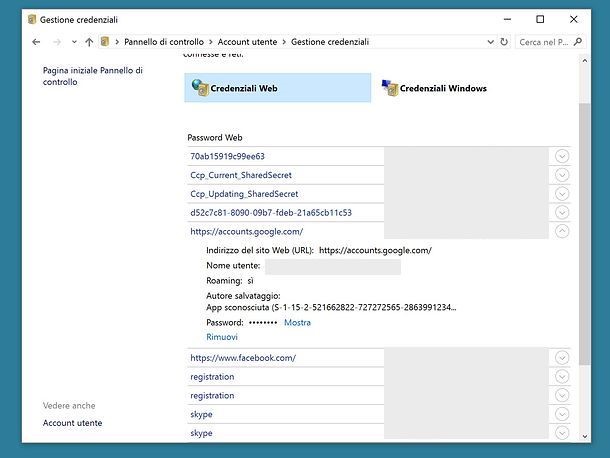
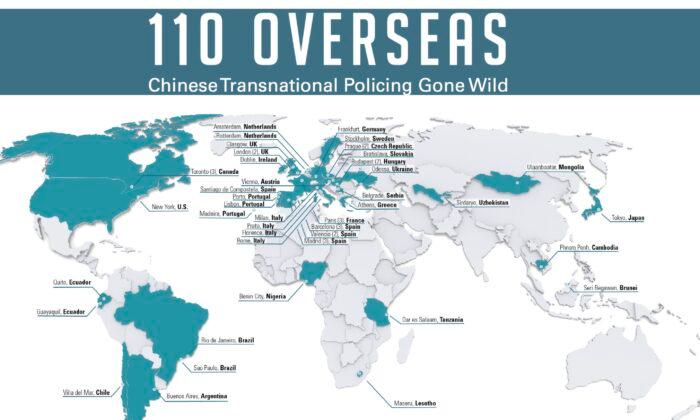
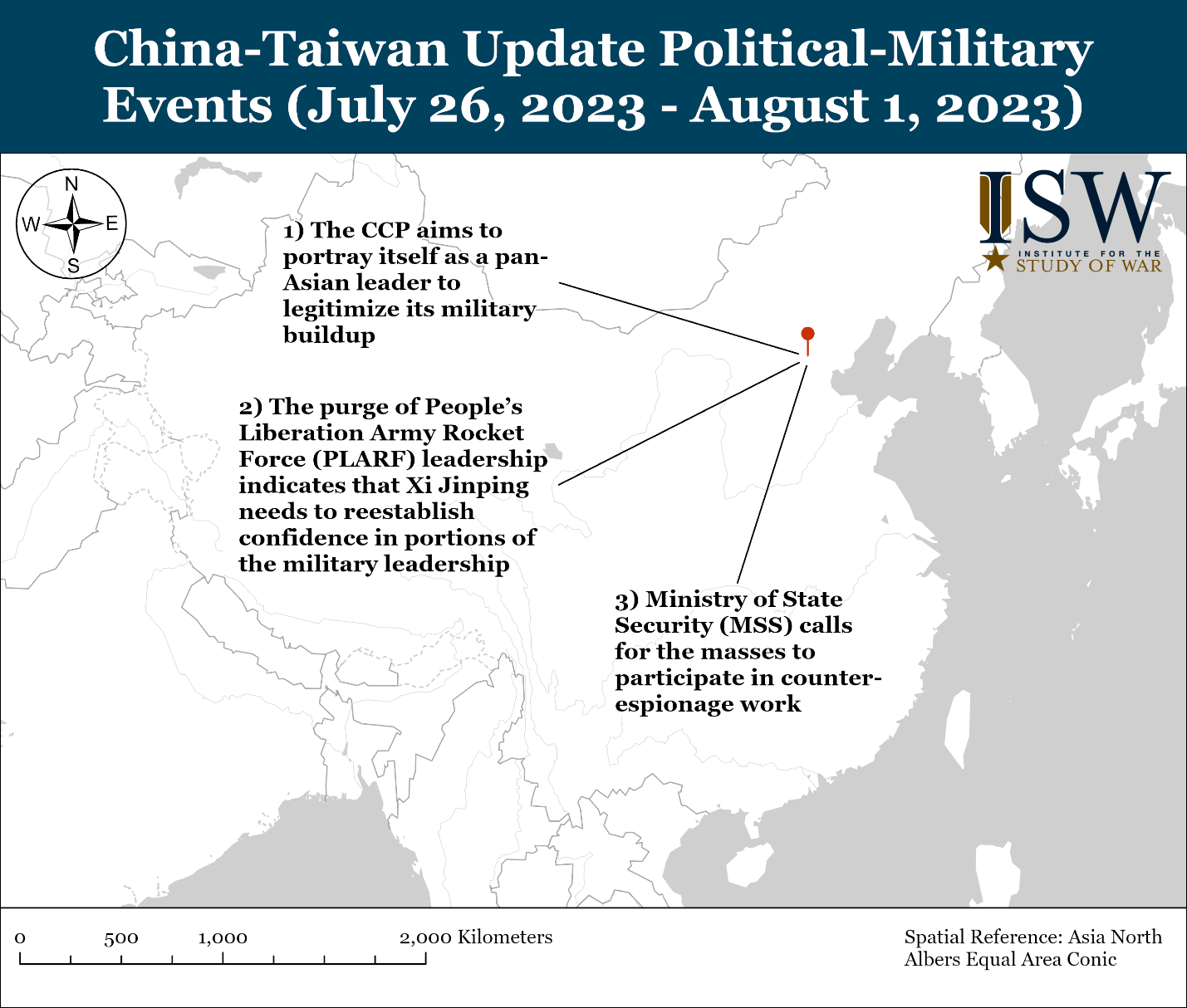
![Investigative Report]How China Uses Hong Kong as a Secret Hub for Global Propaganda through Nouvelles d'Europe - 卡卡、莫莫、M.Y. - 如水 Investigative Report]How China Uses Hong Kong as a Secret Hub for Global Propaganda through Nouvelles d'Europe - 卡卡、莫莫、M.Y. - 如水](https://flowhongkong.net/wp-content/uploads/2023/07/%E4%B8%BB%E9%A0%81%E7%B6%B2%E5%9C%96%E8%8B%B1%E6%96%87.jpg)
Investigative Report]How China Uses Hong Kong as a Secret Hub for Global Propaganda through Nouvelles d'Europe - 卡卡、莫莫、M.Y. - 如水
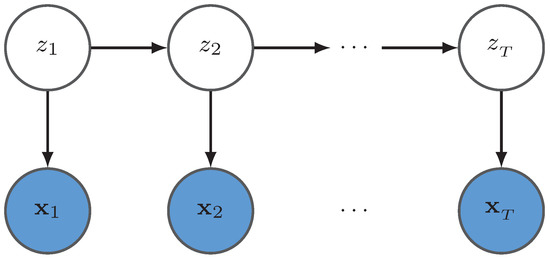
Entropy | Free Full-Text | Variational Beta Process Hidden Markov Models with Shared Hidden States for Trajectory Recognition